Cryptography is one significant element, a major technology that blankets blockchain with ultimate security, making it all tamper-proof. Do you know blockchain makes use of two main cryptographic primitives: Hashing and Digital Signature. We’ve already seen what Hashing is in the previous article.
Now let’s dissect what Digital Signatures is all about.
Well….wait. Before heading towards the Digital Signatures, let’s quickly stroll through a set of terms that closely resides to Cryptography. That helps you better mug the concept.
To start with, let’s see what Cryptography is.
To simply define the term, Cryptography is a kind of “secret writing”. A study of techniques of sending private messages between two without allowing any third party to gain access. Here, the original message (plain text) is converted to an unintelligible form (cipher text) from its readable form. This process is called Encryption.
Decryption refers to the process of recovering the original message from its encrypted format. Apart from the plain text or cipher text, some extra information is also required for encrypting and decrypting the data. This information is known as key.
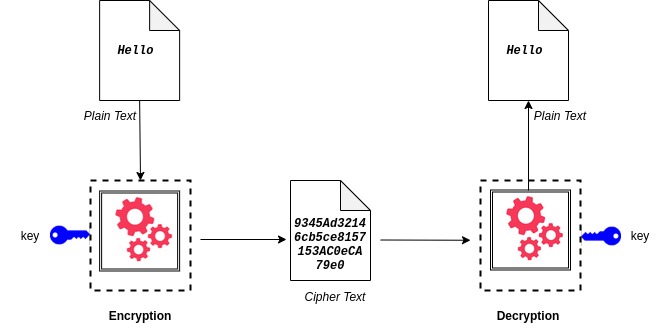
Symmetric cryptographic techniques makes use of the same key for both encryption and decryption. On the other hand, the Asymmetric cryptographic techniques makes use of different keys for encryption and decryption. Modern cryptography relies on mathematical theory and computer science.
Digital Signature
In blockchain, the transactions require a valid signature to be included in the network. Transactions are “digitally” signed. The digital signature is based on public-key cryptography where each user got a key pair consisting of a private key (secret) and public key. While, the public key is similar to a bank account number, the private key is similar to the secret PIN. The public key is used to receive cryptocurrency, and the private key is used to sign transactions to send cryptocurrency.
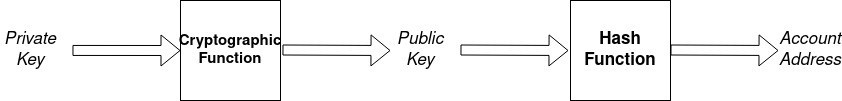
The private key is generated in random. There are various methods for generating a random number. The method used and the length of keys vary according to the cryptographic algorithm.
If you wanna try the random generation of private key, check this link. Public key is derived from private key. This mathematical relationship is the special property that allows the private key to be used to generate signatures on transactions. The signature can be validated using the public key, without revealing the private key. Every participant in a blockchain network is identified by an address which is generated from their public key.
Let’s take a use case.
Let us see how Alice signed the transaction to send 5 cryptocurrency to Bob. Along with the currency, she has a public key and a secret (private) key in her blockchain wallet. To read on wallets, check out our blog on HD Wallets.

It is the digital signature algorithm that generates a signature for the transaction using Alice’s private key.
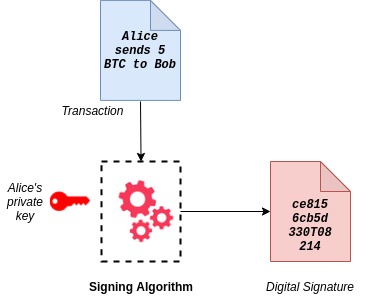
The digital signature depends on the transaction and the private key of the signer. The transaction, signature and copy of the public key is send to the entire blockchain network. Any node in the network can check if the Alice’s signature is valid for the given transaction and public key.
Do you know a digital signature can solve many deficiencies that of a physical signature. To cite, the physical signature that Alice uses to sign her Cheque will be the same for all transactions. In that case, anyone can forge her physical signature and a fake transaction. However, the Alice’s digital signature will be different for different transactions. Alice’s signature on her transaction to Charley will be different from that of the signature she used for Bob. The signatures on further transactions from Alice to Bob will also be different.
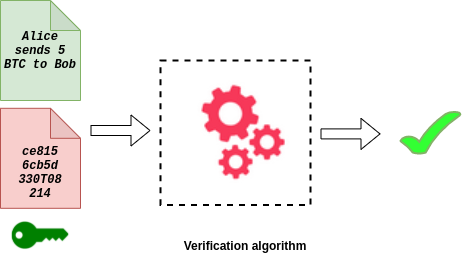
One need not worry about forging their digital signature. That will be identified during the verification process.
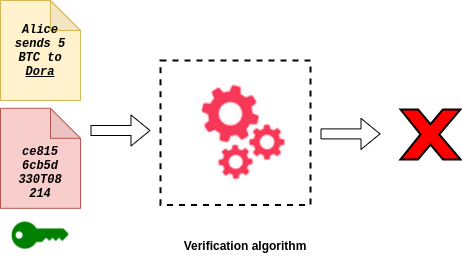
Here a fake transaction to Dora was circulated in the network, copying Alice’s signature from her previous transaction. But the verification algorithm matches the signature against the message and finds that it is not a valid signature for Dora’s transaction. Thus it will be rejected by the network.
Does that mean anyone can pretend to be Alice and issue the transactions on her behalf?….Well that’s why it’s advised to keep the private key confidential. The private key must remain secret always because revealing it to a third party is equivalent to giving them control over the funds secured by that key. If anyone gets access to Alice’s secret key, that person will be able to manipulate the funds of Alice.
Cryptography relies on several complicated mathematical functions which are hard to break in actual practice by any adversary. Though the cryptographic computations used in blockchain are easy to calculate in one direction, it is infeasible to calculate in the opposite direction. Bitcoin uses elliptic curve multiplication as the basis for its public key cryptography. The public key is calculated from the private key using elliptic curve multiplication. Below is an example of digital signature generated using ECDSA (Elliptic Curve Digital Signature Algorithm), which is used by Bitcoin.
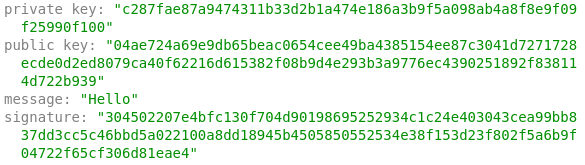
Check this link for a demo of digital signatures. Please note that the keys and signature shown in the examples are for demonstration purpose alone. Do not use it for any blockchain transactions.
